In the 1980s, the European-dominated International Standards Organization (ISO), began to develop its Open Systems Interconnection (OSI) networking suite. OSI has two major components: an abstract model of networking (the Basic Reference Model, or seven-layer model), and a set of concrete protocols. The standard documents that describe OSI are for sale and not currently available online.
Parts of OSI have influenced Internet protocol development, but none more than the abstract model itself, documented in OSI 7498 and its various addenda. In this model, a networking system is divided into layers. Within each layer, one or more entities implement its functionality. Each entity interacts directly only with the layer immediately beneath it, and provides facilities for use by the layer above it. Protocols enable an entity in one host to interact with a corresponding entity at the same layer in a remote host.
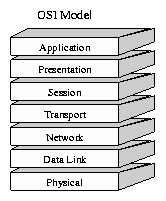
The seven layers of the OSI Basic Reference Model are (from bottom to top):
- The Physical Layer :-Physical layer defines and cables, network cards and physical aspects. It defines raw bit stream on the physical media. It also provides the interface between network and network communication devices. It is also responsible for how many volts for 0 and how many for 1. Physical layer also checks the number of bits transmitted per second and two ways or one way transmission. Physical layer also dealing with the optical, mechanical and electrical features.Protocols: Protocols that work on the physical layer are ISDN, IEEE 802 and IEEE 802.2 Network Devices: Hubs, Repeaters, Oscilloscope and Amplifier works on the network devices..
- The Data Link Layer :-Defines procedures for operating the communication links
Frames packets
Detects and corrects packets transmit errors
Protocols: Logical Link Control
• error correction and flow control
• manages link control and defines SAPs
802.1 OSI Model
802.2 Logical Link Control
Media Access Control
• communicates with the adapter card
• controls the type of media being used:
802.3 CSMA/CD (Ethernet)
802.4 Token Bus (ARCnet)
802.5 Token Ring
802.12 Demand Priority
Network Devices: Bridge
Switch
ISDN Router
Intelligent Hub
NIC
Advanced Cable Tester
- The Network Layer:-The network layer determines that how data transmits between the network devices. It also translates the logical address into the physical address e.g computer name into MAC address. It is also responsible for defining the route, managing the network problems and addressing. Router works on the network layer and if a sending device does not break the data into the similar packets as the receiving device then network layer split the data into the smaller units and at the receiving end the network layer reassemble the data.Network layer routes the packets according to the unique network addresses. Router works as the post office and network layer stamps the letters (data) for the specific destinations. Protocols: These protocols work on the network layer IP, ICMP, ARP, RIP, OSI, IPX and OSPF. Network Devices: Network devices including Router, Brouter, Frame Relay device and ATM switch devices work on the network layer.
- The Transport Layer:-Transport layer manages end to end message delivery in a network and also provides the error checking and hence guarantees that no duplication or errors are occurring in the data transfers across the network. Transport layer also provides the acknowledgement of the successful data transmission and retransmits the data if no error free data was transferred.It also provides and error handling and connectionless oriented data deliver in the network. Protocols: These protocols work on the transport layer TCP, SPX, NETBIOS, ATP and NWLINK.Network Devices: The Brouter, Gateway and Cable tester work on the transport layer.
- The Session Layer:-Session layer establish and manages the session between the two users at different ends in a network. Session layer also manages who can transfer the data in a certain amount of time and for how long. The examples of session layers and the interactive logins and file transfer sessions. Session layer reconnect the session if it disconnects. It also reports and logs and upper layer errors.
Protocols: The protocols that work on the session layer are NetBIOS, Mail Slots, Names Pipes, RPC
Network Devices: Gateway - The Presentation Layer:-The presentation layer presents the data into a uniform format and masks the difference of data format between two dissimilar systems. It also translates the data from application to the network format. Presentation layer is also responsible for the protocol conversion, encryption, decryption and data compression. Presentation layer is a best layer for cryptography. Network Devices: Gateway Redirector is operates on the presentation layer.
- The Application Layer :-The application layer defines the interfaces for communication and data transfer. This layer also provides and support services such as job transfer, handles network access, e-mail, supports user applications and error recovery.Protocols: FTP, DNS, SNMP, SMTP, FINGER, TELNET, TFTP, BOOTP and SMB protocol are operated on the application layer.Network Devices: Gateway network device is operated on the application layer.
DoD Networking Model
The Department of Defense Four-Layer Model was developed in the 1970s for the DARPA Internetwork Project that eventually grew into the Internet. The core Internet protocols adhere to this model, although the OSI Seven Layer Model is justly preferred for new designs.
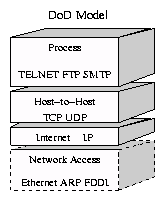
The four layers in the DoD model, from bottom to top, are:
- The Network Access Layer is responsible for delivering data over the particular hardware media in use. Different protocols are selected from this layer, depending on the type of physical network.
- The Internet Layer is responsible for delivering data across a series of different physical networks that interconnect a source and destination machine. Routing protocols are most closely associated with this layer, as is the IP Protocol, the Internet's fundamental protocol.
- The Host-to-Host Layer handles connection rendezvous, flow control, retransmission of lost data, and other generic data flow management. The mutually exclusive TCP and UDP protocols are this layer's most important members.
- The Process Layer contains protocols that implement user-level functions, such as mail delivery, file transfer and remote login.


Very informative post. Keep up the good work. I would really look forward to your other posts
ReplyDeleteDell - Inspiron 15.6" Touch-Screen Laptop - 4GB Memory - 500GB Hard Drive - Black (15RVT-9095BLK)
Dell - Latitude 14.1" Refurbished Laptop - 4GB Memory - 250GB Hard Drive - Gray